Veritas Storage Foundation Software Checks
- Veritas Software Corporation
- Veritas Storage Foundation Software Checks Reviews
- Veritas Storage Foundation Software Checks For Business
Symantec Storage Foundation you can download for your learnig and practice and also you can see and test the features of the Products http:-aikitsupport.com for more info Check Out the Link.
Check Point Reference: CPAI-2008-332 Date Published: 2 Nov 2009 Severity: Critical Last Updated: 2 Nov 2009 Source: Industry Reference: Protection Provided by: Security Gateway R80, R77, R76, R75 Who is Vulnerable? Vulnerability Description Symantec Veritas Storage Foundation for Windows (SFW) is a storage management suite. Building construction handbook free pdf. With a set of networks services and client agents, the product provides solution for online heterogeneous storage management. One of the services installed by SFW is the Veritas Scheduler Service, implemented in executable binary file VxSchedService.exe. This service listens on TCP port 4888 by default.A security bypass vulnerability exists in Symantec Veritas Storage Foundation Scheduler Service. The vulnerability is due to improper handling of NTLMSSP authentication. Remote unauthenticated attackers could exploit this vulnerability by using NULL NTLMSSP authentication to manipulate snapshots, their schedules, and run other potentially unsafe disk manipulation commands on the target server.
Successful exploitation could lead to arbitrary code execution in the security context of the SYSTEM user.An attack targeting this vulnerability can result in authentication bypass and command execution to the target system. In an attack case where command execution is successful, the behaviour of the target is entirely dependent on the intended function of the executed commands.
Veritas Software Corporation
The code in such a case would execute within the security context of the running process, normally System. Protection Overview This protection will detect and block attempts to exploit this vulnerability In order for the protection to be activated, update your Security Gateway product to the latest IPS update.For information on how to update IPS, go to, click on Protection tab and select the version of your choice. Security Gateway R80 / R77 / R76 / R75. In the IPS tab, click Protections and find the Symantec Veritas Storage Foundation Scheduler Authentication Bypass protection using the Search tool and Edit the protection's settings. Install policy on all modules. This protection's log will contain the following information: Attack Name: Application Servers Protection Violation Attack Information: Symantec Veritas Storage Foundation Scheduler authentication bypass.
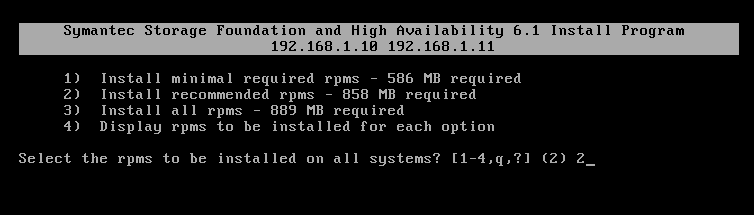
To configure Storage Foundation product on a cluster. To invoke the common installer, run the installer command with the configure option, as shown in this example: #./installer -configure. When the list of available products is displayed, select Veritas Storage Foundation (SF), enter the corresponding number, and press Return.
Select a product to configure:. You are prompted to enter the system names (in the following example, 'host1' and 'host2') on which the software is to be installed. Enter the system name or names and then press Return. Enter the system names separated by spaces on which to configure SF: host1 host2.
During the initial system check, the installer checks that communication between systems has been set up. The installer requires that ssh commands used between systems execute without prompting for passwords or confirmations. If the installer hangs or asks for a login password, stop the installer and run it again with the ssh configured for password free logins, or configure rsh and use the -rsh option. The procedure checks system licensing, and you can enter additional licenses, if needed. Checking system licensing SF license registered on host1 Do you want to enter another license key for host1? y,n,q (n) n.
When prompted to configure VCS, enter y to configure VCS on these systems. Do you want to configure VCS on these systems at this time? y,n,q (y) y No configuration changes are made to the systems until all configuration questions are completed and confirmed.
Press Return to continue. All systems are configured to create one cluster. Enter the unique cluster name and Cluster ID number. Enter the unique cluster name: ?
cluster2 Enter the unique Cluster ID number between 0-65535: b,? 76. The installer discovers the network interfaces (NICs) available on the first system and reports them: Discovering NICs on host1. Discovered eth0 eth1 eth2 eth3. Enter private heartbeat NIC information for each host. Enter the NIC for the first private heartbeat link on host1: b,?
eth1 Would you like to configure a second private heartbeat link? y,n,q,b,?
(y) y Enter the NIC for the second private heartbeat link on host1: b,? eth2 Would you like to configure a third private heartbeat link?
y,n,q,b,? (n) n Do you want to configure an additional low priority heartbeat link? y,n,q,b,?
(n) n Are you using the same NICs for private heartbeat links on all systems? y,n,q,b,? (y) y. Warning: When answering y, make sure that the same NICs are available on each system; the installer may not verify this.
The NICs should also be the same speed on both systems for the heartbeat links to function properly. Notice that in this example, eth0 is not selected for use as a private heartbeat NIC because it already in use as the public network interface. A summary of the information you entered is given. When prompted, confirm that the information is correct. Is this information correct? y,n,q If the information is correct, enter y.

Veritas Storage Foundation Software Checks Reviews
If the information is not correct, enter n. The installer prompts you to enter the information again. When prompted to configure the product to use Veritas Security Services, enter n, unless a Root Broker has already been set up. Warning: Before configuring a cluster to operate using Veritas Security Services, another system must already have Veritas Security Services installed and be operating as a Root Broker. Refer to the Veritas Cluster Server Installation Guide for more information on configuring a VxSS Root Broker. Would you like to configure SF to use Symantec Security Services?
y,n,q (n) n. To add users, you will need the user name, password, and user privileges (Administrator, Operator, or Guest).
Veritas Storage Foundation Software Checks For Business
When prompted, set the user name and /or password for the Administrator. Enter n if you want to decline. If you enter y, you are prompted to change the password. Do you want to set the username and/or password for the Admin user (default username = 'admin', password='password')? y,n,q (n) n. You are prompted to add another user to the cluster.
Enter n if you want to decline, enter y if you want to add another user. Do you want to add another user to the cluster? y,n,q (y) y. You are prompted to enter the user information. Enter the user name: ? myuser Enter New Password: Enter Again: Enter the privilege for user myuser (A=Administrator, O=Operator, G=Guest): ?
A. Enter y or n to verify if this information is correct. Is this information correct?
y,n,q (y) y. When prompted to configure SMTP notification, enter n or y to configure.
To configure SNMP notification, enter the following information. You can then confirm that it is correct, or enter it again. Do you want to configure SMTP notification?